Hacking: The Next Generation is an extremely good book filled with detailed examples on how hackers maliciously attack unsuspecting users. While this book primarily discusses the offensive strategies hackers employ, I am going to discuss several countermeasures to help secure mobile users. Mobile vulnerabilities typically fall under one or more of the following categories:
WIFI Hacks
TJ Maxx suffered a $4.5 billion data breach because they had a WIFI security vulnerability in one of their stores. WIFI networks can be extremely insecure and they provide hackers two attack options.
Passive Attacks
Passive attacks are when hackers utilize tools to scan the WIFI network for streams of personal data. The hacker is hoping an unaware user will enter personal information from a non-secured web site. For example, MySpace still allows users to log in unsecured (non-https). Your user credentials will pass the wire in clear text! The hacker may attempt to retry those same credentials against your email, corporate, and personal banking sites. Social networking sites often expose these personal details. One potential solution is to never re-use your credentials across multiple sites. Better yet, never enter personal information over an insecure network!Active Attacks
Active attacks are when hackers setup rogue access points on a WIFI network. From this approach, the hacker is hoping an unsuspecting user connects to their malicious access point. If a connection is established and the unsuspecting user ignores the security vulnerability warnings, the hacker has access to all your personal data even over a secured (https) site.Defending WIFI attacks
- Never enter personal information from insecure (non-https) sites. Look for either "https" within the browsers URL or look for the locked image icon
 within your browser to determine if the site is secure. Browser warnings can also be configured to alert users when they are not on a secured site.
within your browser to determine if the site is secure. Browser warnings can also be configured to alert users when they are not on a secured site. - Validate you are connected to a trusted WIFI access point. Most browsers can protect and alert users of this attack. For example, from IE you would see a warning shown in Figure 1 below. However, most users may not completely understand the warning and may ignore it completely. For example, if you need to board a plane in 15-minutes and need to send an urgent email what do you do? In IE, the security setting to enable this check is shown in Figure 2 and is enabled by default.
- Validate strong encryption is used on your wireless network. WPA is preferred. For example, if you are still using WEP encryption for your home wireless network you should upgrade. There are tools that allow hackers to crack WEP encryption relatively quickly.
- Encrypt sensitive documents. Encryption adds an additional layer of security. If you have personal documents saved locally they should be encrypted. Also, when sending sensitive documents those should be encrypted too.
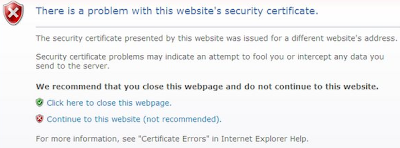
Figure 1.

Figure 2.
Stolen Phone
The most common type of data breach is from physically stolen devices. Forty percent of data breaches fall under this category. Additionally, hackers may use CSI sticks to extract all data and leave your phone behind. So do not assume that your data has not been tampered with if you still have your phone in hand.
Defending Stolen Phone
- Encrypt sensitive documents!
- Remotely erase your phone if it is lost or stolen. For example, Mobile Defense is an Android app that can remotely find, lock, backup, and erase your phone.
Voice Mail Hacking
Can you access your mobile voicemail from your cellphone without entering a PIN? If you can, you may be susceptible to caller ID spoofing. Make sure a PIN is required for all voicemail access. Nitesh Dhanjani has a detailed blog posting about this attack.





